 We keep RSFirewall! inline with the evolving attacking methods, thus we’re releasing this new revision - 18, with improved XSS (Cross-site scripting ) and LFI (local file inclusion) detection methods.
We keep RSFirewall! inline with the evolving attacking methods, thus we’re releasing this new revision - 18, with improved XSS (Cross-site scripting ) and LFI (local file inclusion) detection methods.
Updated XSS detection
In the new revision, RSFirewall! relies on an increased range of XSS filtering and uses extra triggered actions to block XSS attacks. The attacks are automatically blocked.
Why is important to protect your Joomla! website by XSS attacks?
XSS attacks affect the end user, not the website itself because of the improperly variable validation in web applications, thus allowing to run arbitrary code (JavaScript, HTML, Flash, etc) on the user computer.
The result? Account hijacking, cookie theft and other private information compromised.
More information about XSS:
Joomla! Security Useful security tips for your website, by RSJoomla.com - chapter 1.5 Cross Site Scripting
XSS Statistics:
“Statistically, 42% of web applications which request security audits are vulnerable to XSS, which is clearly the most recurring high-risk exploit among all the applications tested. ” according to www.acunetix.com
Updated LFI detection
When attackers are trying to load a file as being a Joomla! component controller for example, the RSFirewall! Active Scanner is triggered, thus blocking any malicious attempt.
Why is important to protect your Joomla! website by LFI attacks?
A local file inclusion allows to execute arbitrary files as code, the file being loaded locally, from the disk. The result? Well... you can just imagine what an attacker can do by executing almost any code onto your site.
LFI statistics
According to www.exploit-db.com, in 2010 were detected 122 web applications with local file inclusion vulnerability, from which 89 were Joomla! extensions.
RSFirewall! Active Scanner - LFI settings:
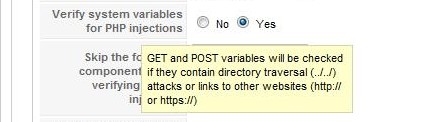
XSS and LFI attacks are automatically blocked by RSFirewall! so you and your business are as protected as possible.
Changelog: 29.07.2010 - Rev 18
Click to view the complete changelog.

