System Check - Security Scanner for Joomla!
The System Check is an on-demand scanner that performs an extensive scan of your Joomla! installation. The scanner is divided in 3 main sections: Joomla! Configuration, Server Configuration and File Integrity.
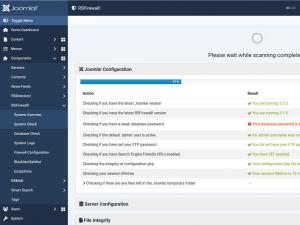
Joomla! Configuration
- Joomla! and RSFirewal! versions: checks whether you are using the latest versions of RSFirewal! and Joomla!. If newer versions have been released it also provides a download link to the specific patch.
- Database password: checks whether the database password offer a good level of security against brute-force attacks.
- Default admin: checks whether the default "admin" user is in use and if the username and password offer a good level of security against brute-force attacks.
- FTP password: if you store your FTP password in the Global Configuration you leave your FTP exposed. Anyone who can access the Global Configuration will be able to retrieve your password and access your FTP account.
- SEF: checking if you have Search Engine Friendly URLs enabled and by enabling SEF in your Joomla! Configuration your website will not be vulnerable to Google searches. An attacker could search on Google for a vulnerable extension (by using the syntax "inurl: option=com_dummy") and target all sites that have it installed.
- configuration.php integrity: checks the integrity of your configuration.php file to be correct.
- Admin users passwords: checks your other website admins to have a proper password which offer a good level of security against brute-force attacks.
- Session lifetime: if you setup your session lifetime too high, you will be vulnerable to prying eyes. It's recommended to keep a lower session lifetime so it will expire early in case you leave your computer.
- Temporary files: checks if you have files left in your Joomla! temporary folder.
- Checking for .htaccess: a preconfigured htaccess file (htaccess.txt) is delivered with Joomla! which you have to rename it into .htaccess. This contains instructions to avoid common exploits and SEF implements.
- Checking if website is blocklisted: the check is performed against Google Safe Browsing lists - to use this you'll need to generate an API key.
Server Configuration
Checks for security flaws in the general PHP configuration. The following items are checked:
- allow_url_include: this option allows the use of URL-aware fopen wrappers with the following functions: include(), include_once(), require(), require_once(), thus enabling an attacker to include his own PHP scripts.
- open_basedir: restricts access to specified directories only.
- disable_functions: disables certain PHP functions. It is recommended to disable: system, shell_exec, passthru, exec, popen, proc_open.
- expose_php: this could allow attackers to retrieve information about your PHP version and we recommend setting this Off.
Attempt to fix PHP Configuration: RSFirewall! will attempt to fix your PHP settings if the configuration is not secure by creating a local php.ini file in the root of your hosting account. If the hosting provider allows this, the php.ini file will be read and the new settings will take effect. If it does not work, then it means that the hosting provider does not allow the reading of local php.ini files. Please directly contact your hosting provider and/or system administrator in order to get this enabled.
File Integrity
This scans the integrity of your Joomla! (CMS) files while also scanning your files for common malware.
Checking if Joomla! core files have been altered in any way. It compares the actual file with a pre-calculated hash of the original core file. The files that have been modified are displayed individually along with the path to that particular file. The File Integrity check is not only a detection tool, but also offers a mechanism that tries to repair the detected problem.
RSFirewall! also allows you to view the differences in modified core Joomla! files. When performing a System Check, the differences will be displayed after pressing the "View differences" button within the Details section of Scan Results.
The original file can be automatically downloaded by clicking on the "Download original" button associated with your modified file within the Details section of Scan Results.
RSFirewall! only includes hashes for the latest available Joomla! 3 version. Whenever a new Joomla! version gets released, the old hashes will get replaced in the RSFirewall! package. If you install RSFirewall! on an older Joomla! version, the hashes will be updated on your installation once you run the System Check. An active license and a valid license code are required for the update to work. If the license code is not valid, you will get the following message:
The File Integrity will also check the followings:
- Folder permissions: checks if the folders contained within your Joomla! installation have the recommended read / write permissions. If any folder does not pass the test it is displayed individually along with a path to the file. Here too, a repair tool is provided however, because of some restrictions that may reside on your server, the tool may or may not succeed. All folders with permissions higher than 755 will be highlighted;
- File permissions: all files with permissions higher than 644 will be highlighted;
- Malware patterns: checks for shell patterns inside files and check for a list of known malware files. Malware, short for malicious software, is software designed to infiltrate or damage a system without the owner's informed consent;
Note: folder permissions are addressed only for UNIX OS, not for IIS servers.
Each of these items have a score that RSFirewall! uses to compute a security grade, so you can get an idea of how secure is your website and take the necessary measures to improve it.
The last successful run of the System Check will be displayed within a blue box at the top of the "System Check" section.
Watch video tutorial
6 persons found this article helpful.
You Should Also Read
Malware Patterns Check |
Joomla! Configuration |
Database Check |
The System Check will not stop |